░D░A░T░A░B░A░S░E░ ░S░E░C░U░R░I░T░Y░
DATA SAFE: Data safe which act as a unified security control. Data safe actually helps us in identifying the gap and the configuration drift within our data structure e.g. Data breach, user’s configuration and the sensitive data.
Data safe work with ALL oracle database, whether it is On-premises and in
Oracle Cloud platform on both.
Suppose if we have some security base line like as a DBA or as a head of
organization we always wanted to set the base line and then if something has
drifted from that base line we need to know. And then we will see whether we
should go with the existing base line in terms of security concern, or we want
to adopt whatever changes we have made.
We can also get information about Privileges & Role for different users so that it can create the profile of all the user’s what kind of activities these users are performing. It will audit on all the actions of those users. We can also discover the sensitive data. And if required For the non-production environment we can mask the Data so that whenever we are allowing other user to work on the non-production environment the data is not replicated from production as such.
“Everything is possible with the help of Data Safe without any expertise
in database security”..!!
The idea of Data Safe is making security so simple for the end users. So
that they do not really need to highly skilled professionals to work on the
data set.
|
v
For Oracle Cloud Infrastructure (OCI) based
Oracle-Databases, Data Safe is free to start with (Until 1Mil Audit Record
and 1K jobs per database per month, subsequently, 0.08 cents for every 10,000
audit records). Once exception to this, Oracle Databases in OCI-compute IaaS
virtual machines are chargeable @ $200. For on-premises database, US$ 200 per
database per month, with same pricing metrics as stated above. v
Data Safe for Database Cloud Service - @Each
are Free /Target per month. |
v
DATA Safe provide us the 5 Main components from the single integrated
console and these components are as follow:
Ø
Security Assessment
Ø
User Assessment
Ø
Activity Auditing
Ø
Data Discovery
Ø
Data Masking
Data Safe also provide the inductive dashboard which give us the critical metrics to know the overall help of your database security postures. So from dashboard we can also drill down into the specifics. If we need to really know what all activities users has done within those what are the admin activities or user assessments. So we can drill down from this dashboard to get the more details about specific.
Ø Security Assessment: It tells us about the configuration, whether this configuration as per oracle best practice or not. Also there are some users which are using the default password, some users which have never actually change their user password or whatever best practices oracle suggest for the database those are there. These reports will also help us in getting the compliance for the Industry standards. Data Safe will actually recommend us how we can remedy existing database security issues.
Ø
User
Assessment: It gives us the clear visibility around the user’s privileges &
roles from a single dashboard and also what are the different activities those
users had performed in the past. We can just go into data safe console dashboard
and drill down to get all the details whatever the changes users are making
those changes are available. And if require we can amend the necessary
privileges from this console.
Ø
Activity Auditing: Data safe allows us to
configure and collect audit data and it can also give you the report. We can
keep these report for any forensic purpose if required in the future. It also
give us the option to remove our older audit log from the database itself if we
want to. For e.g. by default Audit Data Retention Period is 6
months.
·
Reports amount and type of sensitive data
Ø Data Masking: On sensitive data we can create a Data Masking definition applicable. We can do data masking on non-production environment. There are multiple format on which we can do masking and also we can get the report on these masking as well through Data Safe.
CAUTION: - It is one way process non-recoverable. Masking will destroy the original data. “Don’t allow masking privileges to the Data Safe account in a production”.
v Provision and Register an Autonomous Database with Data Safe:
Step 1:
|
(i) Login into your OCI Console. (ii) Go to navigation Menu and select “Autonomous Transaction Processing”.
(iii)
Check in Filter section workload type should be -> Transaction Processing or All so that we
can see our database listed after we create it. And Select our Compartment. Note: To create New Compartment if you want to then follow below
link https://dbasarfaraz.blogspot.com/2020/11/creating-compartment-vcn-subnet-route.html?m=0
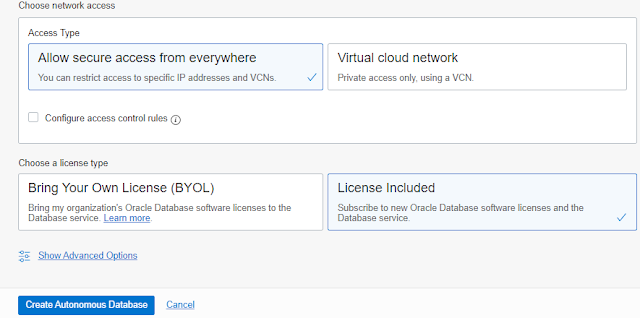
(iv) Click Create Autonomous Database. Fill the Autonomous Database Details page as displayed below: |
STEP 2: Register your Autonomous Database with Oracle Data Safe
(i)
On the Autonomous Database Information tab,
under Data Safe, click Register. If there is no Register option,
that because we are working in a region that does not have the Oracle Data Safe
service enabled in it. If we are the tenancy administrator, please enable
Oracle Data Safe in your tenancy and region. Otherwise, please contact your
tenancy administrator to gain access to an appropriate region.
(ii) In
the Register Database with Data Safe dialog box, click Confirm.
It will
show status: Registered. Now, Click on View. It will redirect you on
Oracle Data Safe Console.
Data Safe Dashboard:
Note: - Our database is listed as a target database. We can view
the list of registered target databases from the Oracle Data Safe service page
in the Oracle Cloud Infrastructure Console.
v On the Home page click on each wizard to access oracle Data Safe main feature:
Click on Security Assessment. It will show the below details.
Click on View Report:
User Accounts
User
Accounts
|
User Name |
Status |
Profile |
Tablespace |
Oracle Defined |
Auth Type |
|
ADMIN |
OPEN |
ORA_ADMIN_PROFILE |
DATA |
No |
PASSWORD |
|
C##API |
OPEN |
DEFAULT |
DATA |
Yes |
PASSWORD |
|
C##CLOUD$SERVICE |
OPEN |
DEFAULT |
SYSAUX |
Yes |
PASSWORD |
|
C##CLOUD_OPS |
OPEN |
DEFAULT |
DATA |
Yes |
PASSWORD |
|
C##OMLIDM |
OPEN |
DEFAULT |
SYSAUX |
Yes |
PASSWORD |
|
DBSNMP |
OPEN |
DEFAULT |
SYSAUX |
Yes |
PASSWORD |
|
DS$ADMIN |
OPEN |
DEFAULT |
DATA |
No |
PASSWORD |
|
GGADMIN |
LOCKED |
ORA_ADMIN_PROFILE |
DATA |
No |
NONE |
|
GRAPH$METADATA |
OPEN |
DEFAULT |
SYSAUX |
Yes |
PASSWORD |
|
GRAPH$PROXY_USER |
OPEN |
DEFAULT |
DATA |
Yes |
PASSWORD |
|
OML$MODELS |
OPEN |
DEFAULT |
SYSAUX |
Yes |
NONE |
|
OML$PROXY |
OPEN |
ORA_APP_PROFILE |
DATA |
Yes |
PASSWORD |
|
OMLMOD$PROXY |
OPEN |
DEFAULT |
DATA |
Yes |
NONE |
|
ORDS_PUBLIC_USER |
OPEN |
ORA_APP_PROFILE |
SYSAUX |
Yes |
PASSWORD |
|
SYSTEM |
OPEN |
DEFAULT |
SYSTEM |
Yes |
PASSWORD |
User Profiles
|
Profile Name |
Parameter |
Value |
|
DEFAULT |
(Number of Users) |
11 |
|
DEFAULT |
CONNECT_TIME |
UNLIMITED |
|
DEFAULT |
FAILED_LOGIN_ATTEMPTS |
10 |
|
DEFAULT |
IDLE_TIME |
UNLIMITED |
|
DEFAULT |
INACTIVE_ACCOUNT_TIME |
UNLIMITED |
|
DEFAULT |
PASSWORD_GRACE_TIME |
30 day(s) |
|
DEFAULT |
PASSWORD_LIFE_TIME |
360 day(s) |
|
DEFAULT |
PASSWORD_LOCK_TIME |
1 day(s) |
|
DEFAULT |
PASSWORD_REUSE_MAX |
4 |
|
DEFAULT |
PASSWORD_REUSE_TIME |
1 day(s) |
|
DEFAULT |
PASSWORD_VERIFY_FUNCTION |
CLOUD_VERIFY_FUNCTION |
|
ORA_ADMIN_PROFILE |
(Number of Users) |
2 |
|
ORA_ADMIN_PROFILE |
CONNECT_TIME |
UNLIMITED (DEFAULT) |
|
ORA_ADMIN_PROFILE |
FAILED_LOGIN_ATTEMPTS |
UNLIMITED |
|
ORA_ADMIN_PROFILE |
IDLE_TIME |
UNLIMITED (DEFAULT) |
|
ORA_ADMIN_PROFILE |
INACTIVE_ACCOUNT_TIME |
UNLIMITED (DEFAULT) |
|
ORA_ADMIN_PROFILE |
PASSWORD_GRACE_TIME |
30 day(s) |
|
ORA_ADMIN_PROFILE |
PASSWORD_LIFE_TIME |
360 day(s) |
|
ORA_ADMIN_PROFILE |
PASSWORD_LOCK_TIME |
1 day(s) |
|
ORA_ADMIN_PROFILE |
PASSWORD_REUSE_MAX |
4 |
|
ORA_ADMIN_PROFILE |
PASSWORD_REUSE_TIME |
1 day(s) |
|
ORA_ADMIN_PROFILE |
PASSWORD_VERIFY_FUNCTION |
FROM ROOT |
|
ORA_APP_PROFILE |
(Number of Users) |
2 |
|
ORA_APP_PROFILE |
CONNECT_TIME |
UNLIMITED (DEFAULT) |
|
ORA_APP_PROFILE |
FAILED_LOGIN_ATTEMPTS |
UNLIMITED |
|
ORA_APP_PROFILE |
IDLE_TIME |
UNLIMITED (DEFAULT) |
|
ORA_APP_PROFILE |
INACTIVE_ACCOUNT_TIME |
UNLIMITED (DEFAULT) |
|
ORA_APP_PROFILE |
PASSWORD_GRACE_TIME |
30 day(s) |
|
ORA_APP_PROFILE |
PASSWORD_LIFE_TIME |
UNLIMITED |
|
ORA_APP_PROFILE |
PASSWORD_LOCK_TIME |
1 day(s) |
|
ORA_APP_PROFILE |
PASSWORD_REUSE_MAX |
4 |
|
ORA_APP_PROFILE |
PASSWORD_REUSE_TIME |
1 day(s) |
|
ORA_APP_PROFILE |
PASSWORD_VERIFY_FUNCTION |
FROM ROOT |
|
ORA_MANDATORY_PROFILE |
(Number of Users) |
0 |
|
ORA_MANDATORY_PROFILE |
CONNECT_TIME |
UNLIMITED (DEFAULT) |
|
ORA_MANDATORY_PROFILE |
FAILED_LOGIN_ATTEMPTS |
10 (DEFAULT) |
|
ORA_MANDATORY_PROFILE |
IDLE_TIME |
UNLIMITED (DEFAULT) |
|
ORA_MANDATORY_PROFILE |
INACTIVE_ACCOUNT_TIME |
UNLIMITED (DEFAULT) |
Inactive
Users
STIG
| Status Low Risk |
Summary Found 6 user accounts that would remain open even if inactive. Found 3 unlocked users inactive for more than 30 days.
Details Users with unlimited INACTIVE_ACCOUNT_TIME: ADMIN, DS$ADMIN, GRAPH$METADATA,GRAPH$PROXY_USER, OML$PROXY, ORDS_PUBLIC_USER
Inactive users: ADMIN, OML$PROXY, ORDS_PUBLIC_USERRemarks If a user account is no longer in use, it increases the attack surface of the system unnecessarily while providing no corresponding benefit. Furthermore, unauthorized use is less likely to be noticed when no one is regularly using the account. Accounts that have been unused for more than 30 days should be investigated to determine whether they should remain active. A solution is to set INACTIVE_ACCOUNT_TIME in the profiles assigned to users to automatically lock accounts which have not logged in to the database instance in a specified number of days. It is also recommended to audit infrequently used accounts for unauthorized activities.
References • Oracle Database 12c STIG v1 r10: Rule SV-76207r2
Click on User Assessment. It will show the below details.

Click on View Report:
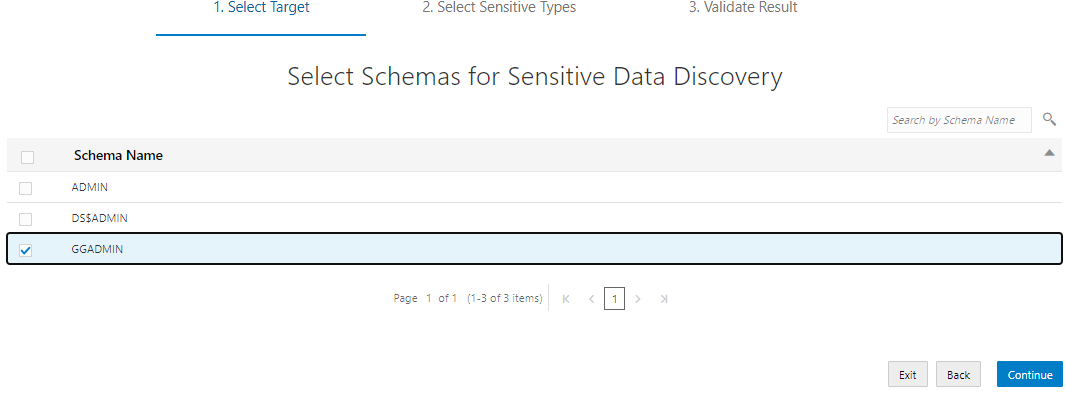
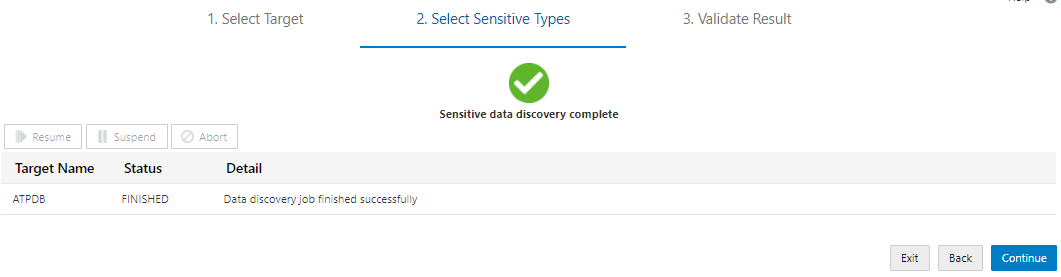
· Now we can Validate result on sensitive data types.






































DB Security is totally new for me...but with your post it's really understandable and easy to read. Thanks for the motivation Sir.
ReplyDeleteIt’s very nicely explained... well done!!!
ReplyDeleteSarfaraz Oracle Dba Blog: Data Safe - Everything You Need To Know (Provisioning And Registration To Target Databases) >>>>> Download Now
ReplyDelete>>>>> Download Full
Sarfaraz Oracle Dba Blog: Data Safe - Everything You Need To Know (Provisioning And Registration To Target Databases) >>>>> Download LINK
>>>>> Download Now
Sarfaraz Oracle Dba Blog: Data Safe - Everything You Need To Know (Provisioning And Registration To Target Databases) >>>>> Download Full
>>>>> Download LINK